FOR MORE INFORMATION CALL
FOR MORE INFORMATION CALL
Your data and assets are constantly evolving. Between mismanaged cloud configurations, expiring certificates, and aging and vulnerable properties, it’s difficult to keep it all up-to-date, and accounted for. Our industry-leading algorithmic discovery and attribution is always on, always seeing, always tracking what’s in your attack surface.
Every minute, your attack surface is expanding. Your external attack surface isn’t simply what you know – it’s a vast, extended, unseen digital world that includes services, hosts, websites, storage buckets and cloud accounts. In this demo, we’ll share with you a real-time look into the makeup of your attack surface.
Censys has the largest and most relevant risk framework in the industry, with over 350 actionable and investigatable risks. Censys ASM allows organizations to customize and tailor risk tolerance based on business needs, so you can tune out the noise and focus on what’s most critical.
After your custom ASM demo, you’ll receive an Attack Surface Report (ASR). Your ASR will show the number of assets, including hosts, certificates, domains, storage buckets, clouds, risky services and more, helping you to prioritize the risks that need the most attention.
We know the internet and cloud better than anyone. By providing an attacker-centric view of all external-facing and cloud assets, we help you fix the problems that will get you breached. Your attack surface is changing all the time, but with Censys ASM, you’ll always stay ahead of it.
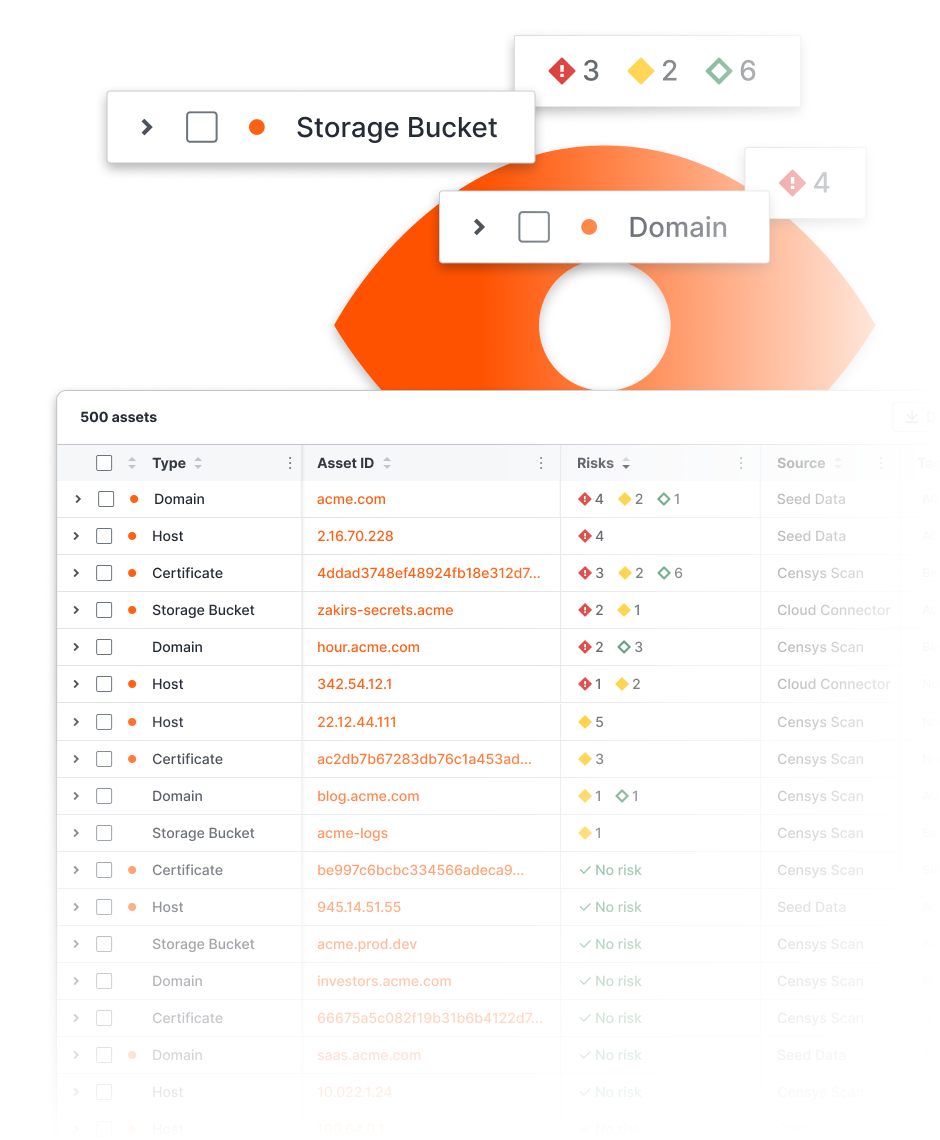
Uncover unknown Internet assets (e.g., hosts, services, SaaS logins, websites, buckets, ICS/IoT devices) regardless of cloud, account, network, or location for the ultimate system of record.
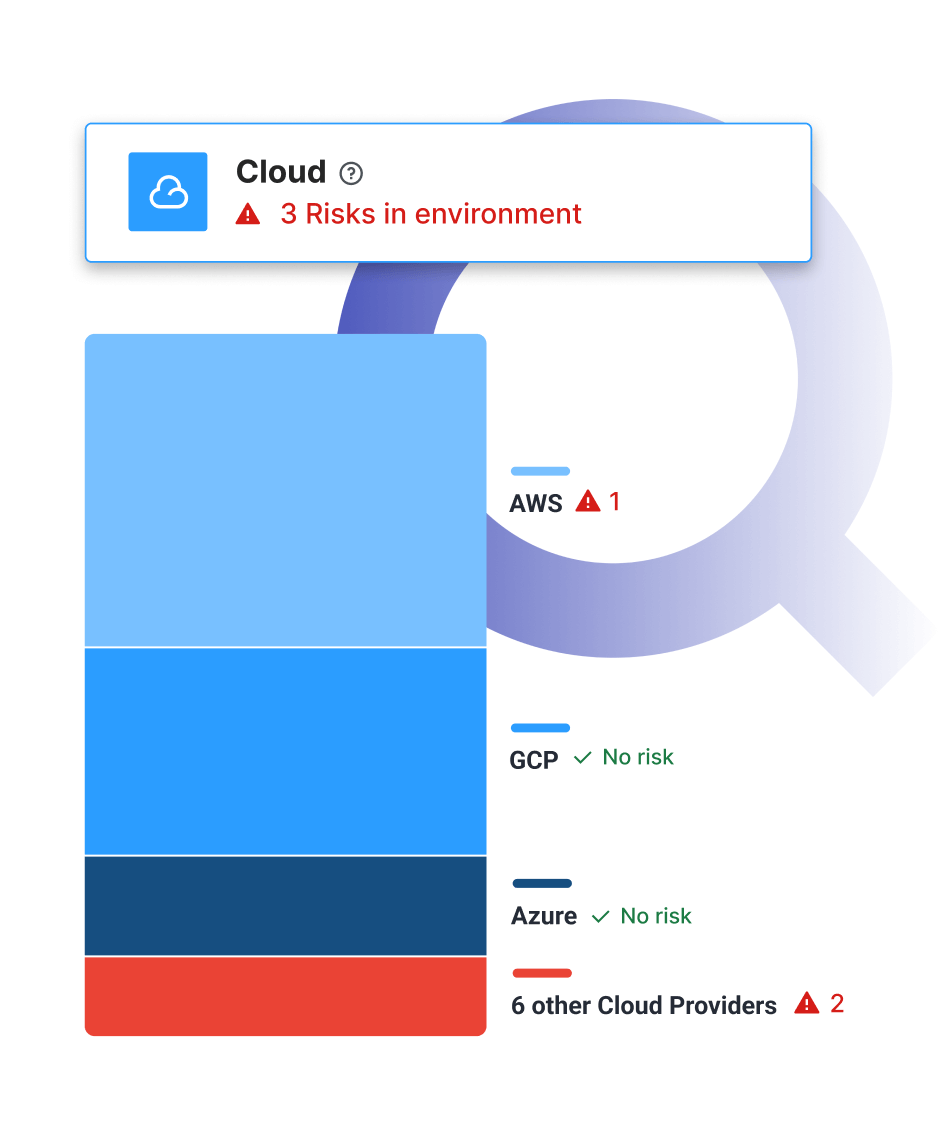
Pinpoint weaknesses in your cloud across all providers, including Amazon Web Services, Google Cloud and Azure.
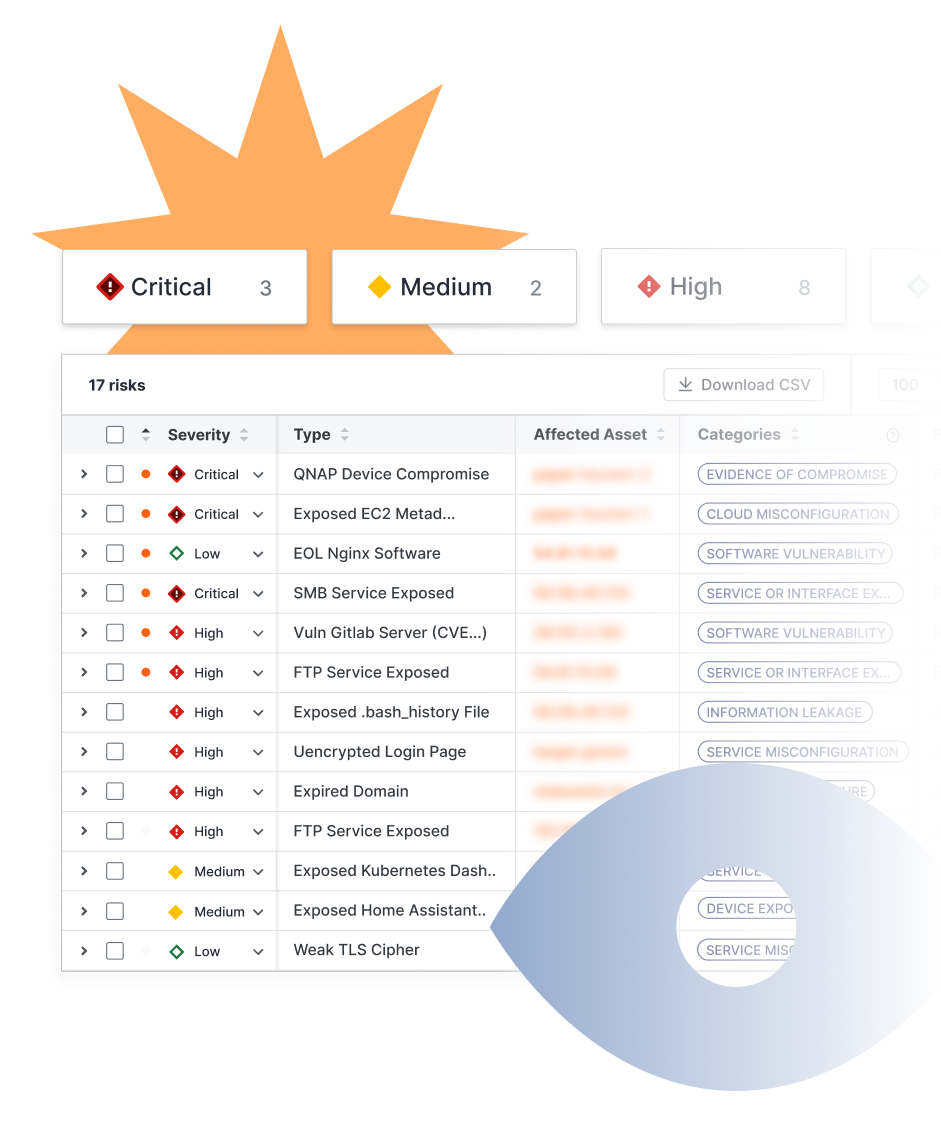
Uncover, prioritize, and remediate critical risks (e.g., potential data loss, critical vulnerabilities, exposed devices/APIs/logins) within hours of coming online.
Rapidly identify and secure Internet assets that may be exploited by a critical vulnerability.
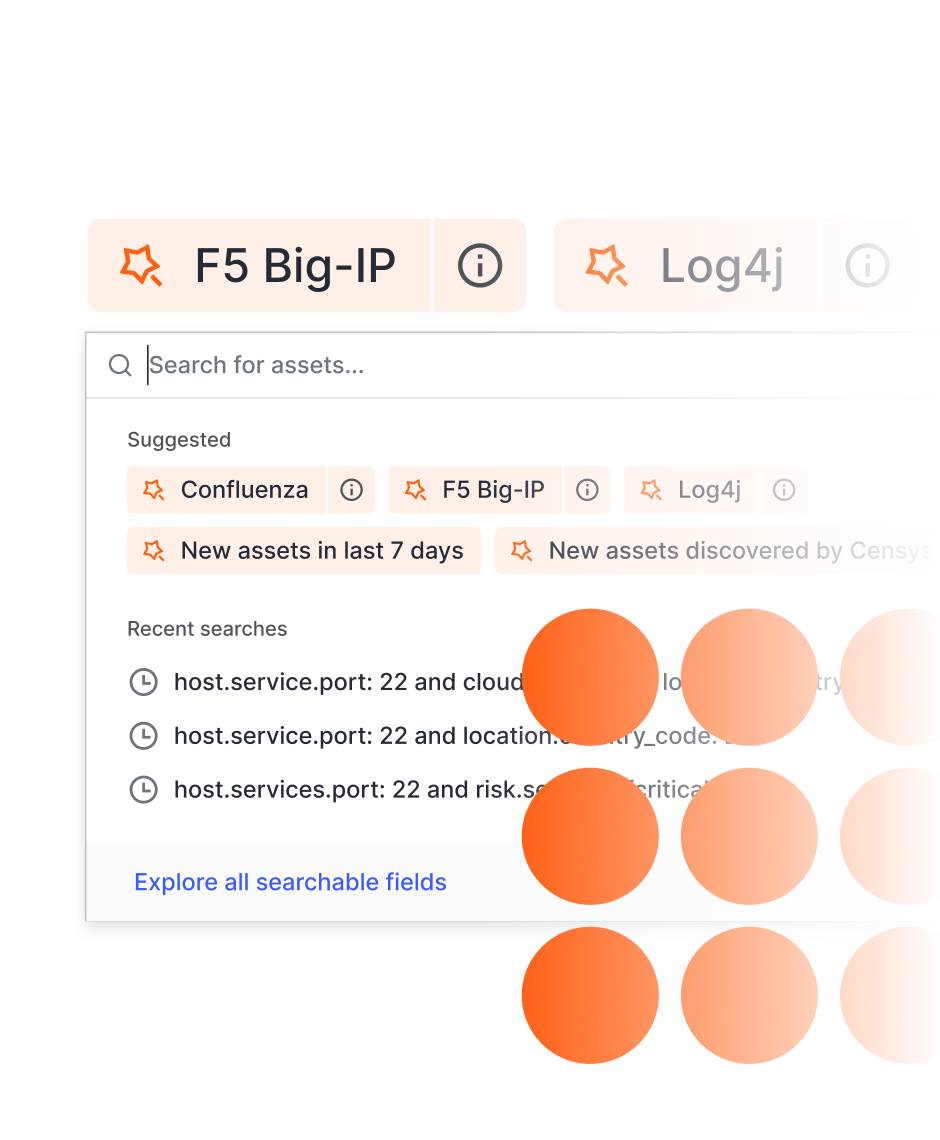

Understand security risk associated with uncontrolled companies — acquisitions, subsidiaries, contractors, and other dependencies.